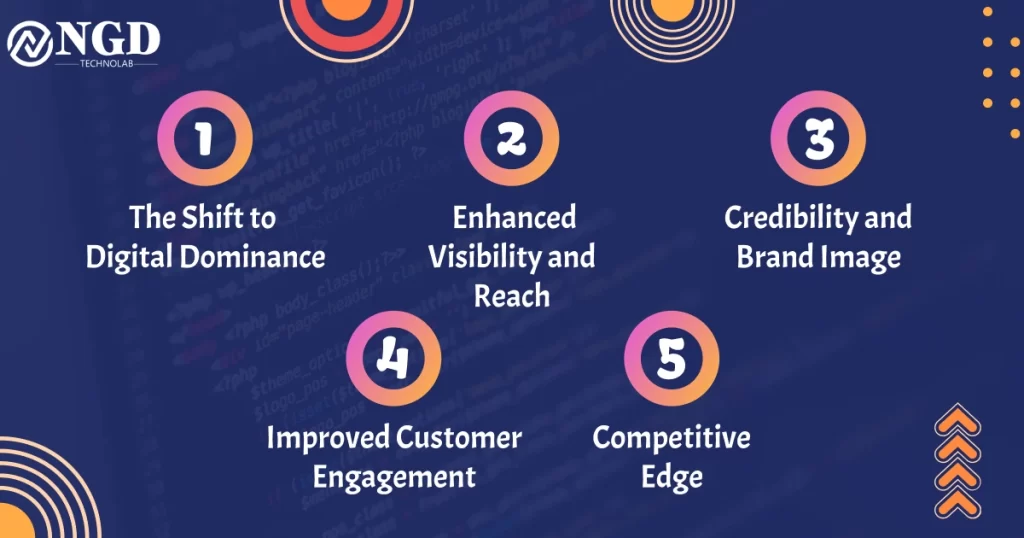
Android App Security Best Practices ( 2025 )
-
 Prashant Padmani
Prashant Padmani

In the fast-changing world of mobile applications, ensuring strong security for Android apps has become more important than ever. As smartphone usage grows, the risk of data theft, hacking, and privacy misuse also increases. This guide explains the best practices for Android app security, helping developers understand how to secure Android apps from hackers, protect user data, and prevent unauthorized access.
1. Android Studio: Unveiling the Power of Android App Developmen
1. Understanding Android App Security
1.1 Introduction to Mobile App Security
Mobile app security plays a vital role during development, especially on Android due to its open-source structure and a wide range of device types. Google offers Android security guidelines to help reduce risks. As more users rely on mobile apps daily, keeping your app secure is essential to protect sensitive data and maintain trust.
1.2 The Significance of Android App Security
Strong security in Android apps helps build user confidence and brand trust. A secure app prevents data leaks, protects personal information, and supports compliance with global data protection laws like GDPR and CCPA.
2. Common Threats and Vulnerabilities
2.1 Data Leaks and Unauthorized Access
One of the most common risks in mobile apps is unauthorized access to user data. Use strong data encryption methods such as AES-256 to protect stored and transmitted information. The OWASP Mobile Security Project lists common threats and recommended solutions.
2.2 Malware and Phishing Attacks
Malware and phishing attacks continue to target Android apps. Use sandboxing, regular malware scans, and tools like Google Play Protect for real-time threat detection.
2.3 Insecure Data Storage
Improperly stored data can be easily misused. Use EncryptedSharedPreferences and Jetpack Security to secure local data. You can also refer to NIST encryption standards for best practices.
2.4 Lack of Secure Communication
Unsecured network communication can expose confidential data. Always use TLS 1.3 to ensure secure, encrypted communication between your app and server.
3. Android Security Features and APIs
3.1 Android Keystore for Secure Key Storage
Android Keystore helps securely store cryptographic keys. When possible, enable hardware-backed security for stronger protection.
3.2 App Permissions and User Consent
Request only necessary permissions based on the least privilege principle. Always explain why each permission is needed. This improves user trust and supports privacy compliance.
3.3 Biometric Authentication
Use biometric authentication for stronger identity verification. Implement BiometricPrompt API to add fingerprint, face, or iris authentication features.
3.4 Secure Socket Layer (SSL) Implementation
Use SSL/TLS encryption and enable Certificate Pinning to prevent man-in-the-middle attacks during data transfer.
4. Secure Coding Practices
4.1 Input Validation and Sanitization
Validate and sanitize user input to prevent attacks like SQL injection and XSS. Tools such as OWASP ESAPI can help.
4.2 Session Management Best Practices
Use secure session tokens, set session timeouts, and require re-authentication for critical account actions.
4.3 Code Obfuscation and Minification
Tools like Android R8 help obfuscate and shrink code to prevent reverse engineering.
4.4 Regular Security Audits and Code Reviews
Conduct regular security reviews and audits to identify weak points early and fix them before release.
5. Testing and Debugging for Security
5.1 Penetration Testing
Perform regular penetration testing to simulate real-world cyberattacks. The OWASP Mobile Security Testing Guide provides detailed methods.
5.2 Static and Dynamic Code Analysis
Tools like SonarQube and Android Lint help detect vulnerabilities during development and testing.
5.3 Real-World User Testing
Beta users can reveal real-time issues that automated scans may miss, improving overall security.
6. Best Practices for Data Encryption
6.1 End-to-End Encryption
Enable end-to-end encryption so data remains secure throughout transmission.
6.2 Encrypting Stored Data
Use AES-256 encryption for stored data and avoid embedding encryption keys in code.
6.3 Transport Layer Security (TLS)
Make sure your app uses TLS 1.3 to ensure secure data transfer.
7. Securing Third-Party Libraries
7.1 Vetted and Updated Libraries
Use trusted, regularly updated libraries to avoid vulnerabilities. Tools like Snyk Security help identify risks.
7.2 Monitoring Library Dependencies
Automate dependency security monitoring using Snyk or Dependabot.
7.3 Regular Security Assessments
Regularly review and assess third-party library security to avoid hidden threats.
8. User Education and Awareness
8.1 Promoting Secure Password Practices
Educate users on creating strong passwords using passphrases and password managers. For example, use at least 12 characters, mix upper and lower case letters, include numbers and symbols, and avoid using personal information.
8.2 Two-Factor Authentication (2FA)
Implement and promote 2FA for accounts handling sensitive information. Learn how users can set up 2FA with Google’s official guide.
8.3 Educating Users on App Permissions
Clearly explain why certain permissions are required to build transparency and trust.
Conclusion
Prioritizing Android app security in 2025 is essential for user trust and long-term success. By applying these best practices, developers can build secure Android apps that protect data and resist cyber threats in an evolving digital environment.
Frequently Asked Questions
Common threats include data leaks, malware, phishing attacks, insecure data storage, and communication vulnerabilities.
Use secure session tokens, enable session timeout, and require re-authentication for sensitive actions.
Penetration testing simulates real-world attacks to uncover vulnerabilities before malicious actors exploit them.
Code obfuscation complicates reverse engineering attempts, protecting intellectual property and sensitive logic.
Users can stay secure by using strong passwords, enabling two-factor authentication, and reviewing app permission requests carefully.
Get Free consultation and let us know about your custom web and Mobile App project idea
Over 14+ years of work experience, we have built 210+ web and mobile apps
We can help you with
- Dedicated Developer
- delivering high-quality development
- Custom Mobile App Development
- Innovative Solution For Startups and Enterprise
Latest Blogs
Explore the Latest Blogs on Trends and Technology.